Some Internet Safety Tips You Must Follow to Browse Securely

Internet Browsers are the most common way to infect your system and steal data. So, if you want to keep your system protected, you must follow browser safety guidelines and use the required tools (if needed). We have listed some useful safety tips/tools below that you should use to browse securely.
Use Incognito/Private Mode While Accessing Sensitive Data
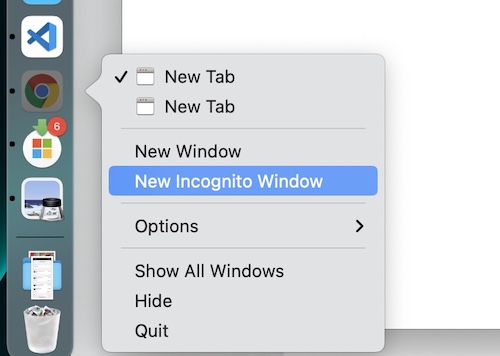
Most modern browsers come with a Private or Incognito Mode. For example, you can right-click on the Google Chrome app icon and select the ‘New Incognito’ option to use it.
Using Private mode is encouraged if you don’t want browsing data (history, form submissions, and cookies) to be saved while you browse. Make this a habit if you are accessing banking or sensitive data.
Use a VPN When Needed
VPNs are useful in many ways. You can hide your IP so no one can get your real identity. By masking your IP address, a VPN ensures that your location, browsing habits, and personal information are not easily traceable by marketers, hackers, or governmental agencies. VPNs can also encrypt internet traffic to let you browse securely. This encryption helps protect your data from being intercepted by cybercriminals, particularly on unsecured networks such as public WiFi, where your information is most vulnerable. Using a VPN is a necessity in these environments to prevent snooping and data theft.
There are different kinds of VPNs available, each offering distinct levels of security and features. Some VPNs use RAM-only servers, which means they only store data on volatile memory that is wiped clean every time they are rebooted, providing an extra layer of security because your information isn’t stored on a hard drive long-term. VPN Surfshark uses this approach, which is particularly beneficial for ensuring that your privacy is maintained even if the server is compromised.
Furthermore, VPNs can unlock content or websites that are blocked in your country as they allow you to select an IP from other countries. This feature is incredibly useful for accessing region-restricted services such as streaming media; for example, you can watch shows on Netflix that are only available in the US by connecting through a US server. This capability not only enhances your security but also your accessibility online, giving you freedom and safety in your digital interactions.
By utilizing a VPN, you effectively secure your online activities and expand your access to global content, making it an indispensable tool for both protection and enhanced internet experience.
Enable 2-Factor Authentication for Internet Accounts
If your emails and internet accounts offer the option to activate 2-Step Verification or 2-Factor Authentication, you must enable it to keep your accounts protected. This way, no one can hack into your account even if they manage to guess the password.
Use a Password Manager
strong passwords enable Google’s 2-step verification.
Using a Password Manager may sound insecure, but it isn’t if you take care of security. Remembering passwords for all accounts is not possible. If you are among those who don’t use a Password Manager, you probably use an easy password to remember them, or you save it in a notepad or somewhere on your computer. Both methods are not secure. You should rather use strong passwords and keep them saved in a Password Manager. You can even use Google Password Manager to save passwords, but just make sure to Enable Google’s 2-step verification.
Block Pop-Up and Redirects
Some websites use Pop-Ups and such ads that open a new browser window and even use redirects to send you to unwanted websites. Most of these pop-up ads target computer users to infect devices with malware, steal data, etc. Pop-ups can be blocked from browser settings. If you are using Google Chrome, you can follow these instructions to disable pop-ups:
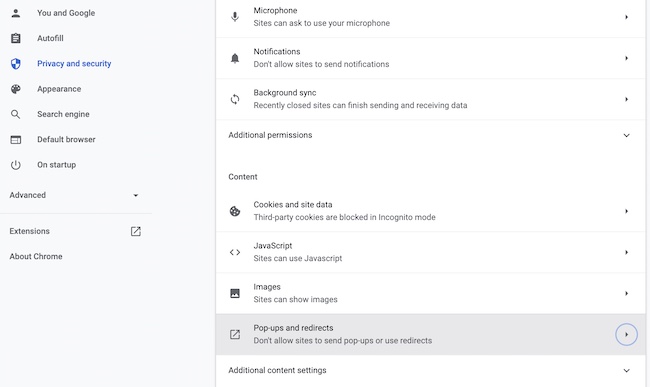
- Click on the options icon (appears in the top right corner of the browser window), then click on the ‘Settings‘ option.
- Select the ‘Privacy and Security‘ option, then click on the ‘Site Settings’ option.
- Pop-ups and Redirects option is located under Content settings. Click on it and then select Don’t allow sites to send pop-ups or use redirects.
Avoid Torrenting
Well, Torrent provides the most reliable download options that almost never fail in the middle, regardless of the file size. You can always pause it and resume from the same point where you left off. However, Torrenting makes your system quite vulnerable to hackers and malware. The items you download from torrents are mostly uploaded by individuals that could be a clean file or an infected file uploaded by a hacker. Downloading from reliable links is not harmful, but using a Torrent Search to look for a random file is never recommended.
Never Install Pirated Software
Pirated software attracts many computer users, but nothing comes free. If someone is working to make paid software available for free, then there is a catch. Pirated software can gain access to your whole computer during the installation process, and you may never realize it. It’s quite easy to hack or snoop into someone’s computer by making them install free software. Stay away from such free or cheap apps! Always download from a reliable app store or trusted app developers’ websites.
Avoid Email Traps
Some common Email Traps include:
- You have WON! (Lottery, Prize, etc.).
- Your Email Storage is almost full, click here to upgrade. Or anything like this.
- You have received Payment, click here to release the payment by completing registration.
- Someone tried to log into your account, please click here to change your password.
These are just some of the examples, but there are many such fraud and spam emails that try to catch your attention and hack your account.
Whenever you receive such emails that claim to be from PayPal, Microsoft, Google, etc., first of all, verify if that email is sent from a reliable email address. For example, emails from PayPal about Payment will never be sent from a gmail.com email. The email must have ‘@paypal.com’ attached to it. If it’s not, it’s a fraud. The link sent within the email must go to the same website as well that you can check in the browser URL (the email may appear as PayPal.com as text and lead to some other website that you can only check by clicking on the link or by copying the URL using right-click). Not clicking on the link is always a better idea when you are in doubt. Just see what it says, and visit the site (if it concerns you) separately by opening a new browser window to verify.
Keep Browser Extensions Updated
Web Browsers allow the addition of extensions/plug-ins, but it’s very important that you keep them updated. Enabling developer mode allows you to install those extensions manually even if they are not in the app store. Install only those extensions that you trust as it can compromise your browser safety.
Regularly Update Your Operating System and Software
Keeping your operating system and software updated is crucial for protecting your computer against attackers who exploit vulnerabilities. Software developers frequently release updates that patch security holes and fix bugs. By ensuring you’re always using the latest versions, you significantly reduce the risk of being compromised by malware that takes advantage of outdated software. Set your system to auto-update wherever possible to streamline this process.
Monitor Your Online Footprint
Be proactive about managing your online presence. Regularly search for your name online and review the information that is publicly available about you. Tighten privacy settings on social media platforms to control who can see your posts and personal details. This reduces the risk of identity theft and fraud, as excessive personal information online can make you an easy target for scammers.
Educate Yourself on Phishing Techniques
Phishing attacks are a common tactic used by cybercriminals to gain access to your personal information. These attacks often involve deceptive emails or messages that mimic reputable sources to trick you into entering sensitive information. By understanding and recognizing the signs of phishing—such as urgent language, unsolicited requests for information, or unfamiliar sender addresses—you can better protect yourself from these types of scams.
Secure Your Home Network
Your home network is a potential entry point for cybercriminals. Start by changing the factory-set default username and password on your router, as these are often easily guessable. Utilize the highest level of encryption available (preferably WPA3) to protect your Wi-Fi network. Consider setting up a separate guest network for visitors; this keeps your main network, which connects your personal devices and stores your information, more secure.
Use HTTPS Websites
When browsing online, ensure that the websites you visit use HTTPS rather than HTTP. The ‘S’ at the end of HTTPS stands for ‘Secure’ and indicates that the website is using encryption—HTTPS encrypts the data sent and received between your browser and the website, which prevents cybercriminals from intercepting this information. Always check for a padlock symbol in the browser’s address bar, which signifies an active secure encryption, enhancing your data protection.