What Is TrueCrypt Encryption Software and How Does It Work? What Are The Best Alternatives To TrueCrypt
Data encryption plays the most important role in maintaining the integrity and confidentiality of data. Many users or organizations prefer to save and share the confidential data in an encrypted form, which can not be manipulated or accessed without authorized access. One of the best examples for such software is “TrueCrypt Encryption software,” that allows users to encrypt the files or hard disk partitions. Therefore, it makes the files unreadable for unauthorized users and helps in maintaining security. In this article, we are going to discuss what is TrueCrypt encryption software, how it works, and its alternative.
What is TrueCrypt encryption Software
TrueCrypt encryption software is an open source tool, that provides encryption of selected files or hard drive partitions. It saves the entire data in an encrypted virtual hard drive, which can be accessed only by the authenticated password. Thus, this software had been widely used among various professionals or users to secure their data by means of encryption. It uses multiple hash algorithms to convert the data into ciphertext so that it becomes impossible for hackers or unauthorized users to access the data. The encrypted TrueCrypt file possess the following characteristics:
- The files can be easily copied, moved or shared without requiring any additional efforts.
- The files can be opened only within TrueCrypt environment by providing the authenticated password.
- When the users access these files, he can edit, delete or copy the files within that folder.
How to Encrypt Data Using TrueCrypt Software
True Crypt is a freeware that can be directly installed to encrypt the particular folders or entire drive partitions depending upon the requirement. It carries out data encryption in the following steps:
- When the app is launched, it displays all the mounted partitions. To create a virtual volume for the partition, click on Create Volume.
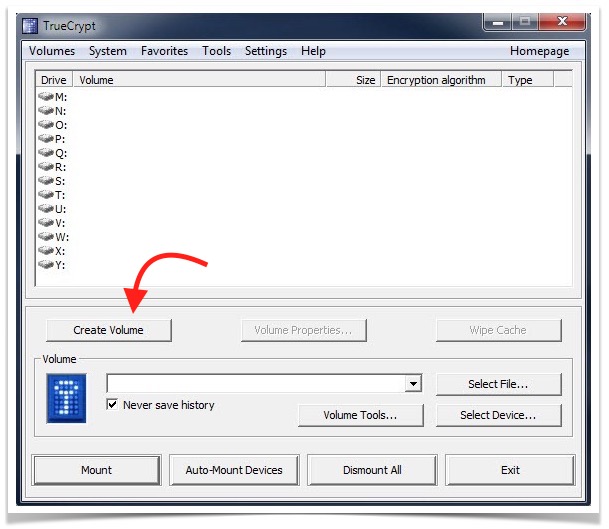
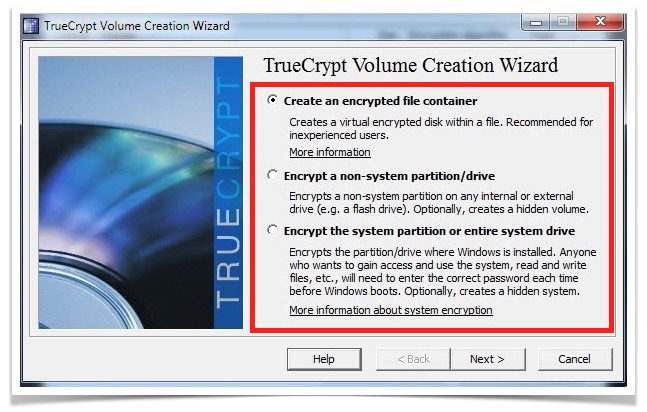
- It generates a TrueCrypt Volume Creation Wizard, which provides 3 options to select the extent of encryption.
- Create an encrypted file container– It is used to generate the encrypted disk within a file itself.
- Encrypt a non-system partition/drive– It is meant to perform encryption on any external drive such as flash drives etc..
- Encrypt system partition or entire system drive– It is used to encrypt the hard drive or its selected partition within Windows.
-
Let’s suppose, we choose to create an encrypted file container option for ease of use. We will select the option “Create an encrypted file container” and click on Next button.
-
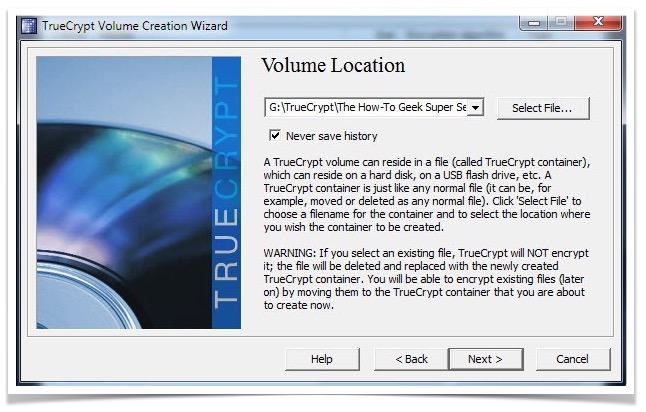
Now Choose the location for saving the generated virtual hard drive, and click Next. Make sure that the chosen location has enough space to create encrypted replica of the selected partition.
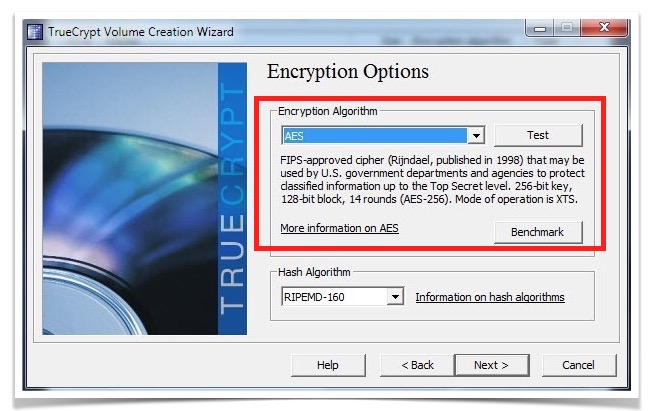
- Under the encryption algorithm window, choose the required algorithms to be used for encrypting data, then click the Next button.
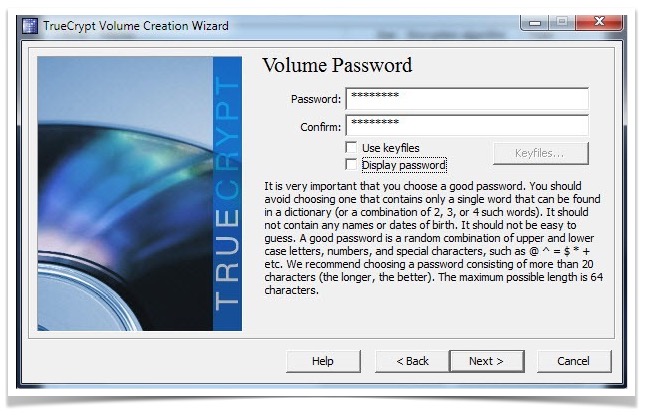
- Enter the password for the generated encrypted TrueCrypt file. This password is to be needed while opening the file.
The above procedure creates a virtual file consisting of the encrypted data without any data loss. The output file with extension .TC can be opened by using the authenticated password.
Issues faced while using TrueCrypt
Although TrueCrypt attempts to maintain the integrity of encrypted data, still it poses certain drawbacks. The major concern is unavoidable loopholes in its security provision. Some of the reasons behind the security issue include:
1. Easy recovery of encryption key
The software maintains the record of encryption keys within system’s RAM. The keys are the major logic behind data security and authentication. So, any hacker or professional can easily extract the keys from memory. Thus, lack of measures to secure keys is a major threat to the software.
2. Lack of physical security
TrueCrypt software does not provide protection against unauthorized physical access. It means that if any hacker gets success in attaining physical access to the system, then the software cannot recognize it.
3. Malware
It does not provide security against malware such as keyloggers, cyber stalking etc.. Thus, anyone can easily detect password and gain access to the virtual files.
Need of TrueCrypt Alternative
After facing certain security hacks as well as legal implications, TrueCrypt had itself declared to suspend the service for users. However, data encryption has become an utmost need of every user nowadays. As a result, users keep on looking for alternatives to TrueCrypt encryption software.
Major Alternative Software for TrueCrypt
1. Bitlocker
It is an inbuilt encryption utility offered by Windows 7 and all the later versions. It encrypts the hard drive to protect confidential data files from unauthorized access. Bitlocker feature can be accessed from Control Panel –> Security –> BitLocker Data Encryption. It possesses the following features that make it a better alternative:
- It offers to provide 128 or 256 bits encryption forth the hard drives.
- It protects data even in the case of malicious data or software installation.
- It recognizes unauthorized physical access and denies such access to files
- Makes sure to encrypt hard drive without any data loss.
2. VeraCrypt
It is a free alternative software, that allows the users to encrypt the hard drive partitions. It aims to eradicate all the major security issues faced while using TrueCrypt. Some of the remarkable features offered by the software include:
- It offers improved encryption algorithms to secure data even in worst conditions.
- It allows to open TrueCrypt files and access its data.
- It is compatible with Windows, Linux, and Mac Operating systems.
3. CipherShed
CipherShed is another alternate encryption software, which has been designed with the basic ideology of TrueCrypt. It offers the following important features, which makes it a prominent choice among users:
- It is designed with advanced hash algorithms.
- It does not store encrypted keys in system memory.
- The software allows to open and view TrueCrypt files.
- This tool is compatible with Windows, Linux, Mac.
Conclusion
With the increasing cyber crimes and cyber attacks, security of data is the major concern for almost every user. One of the prominent ways to maintain data integrity is to encrypt it into the secret code, which cannot be decrypted easily. Thus, many users or professionals attempt to encrypt their confidential data using certain encryption software. Earlier, TrueCrypt had been a solution for most of the users. However, due to certain issues, this service is now outdated. A number of alternate TrueCrypt encryption software are available in the industry, which aims to fulfill user’s expectations to efficiently encrypt data. We have tried to cover the basic details on what is TrueCrypt encryption software, how it works, and its alternatives.